Built for the Enterprise
Dremio is used by 50% of the Fortune 10 and hundreds of the world’s largest companies across all industries. Our customers range from small technology startups to large Global 2000 enterprises in highly-regulated industries such as financial services, insurance, and healthcare, and we are committed to the highest levels of security to meet their stringent requirements and ensure that their data is safe at all times.

Security Assurance
Dremio scans the code of every build for the latest vulnerabilities. We run periodic automated security scans on our daily builds and one-off manual scans as needed. We run both Static Application Security Testing (SAST) and 3rd Party Dependency Checking tools on the code. We also run vulnerability scanners on our containers and images that we create for our products and services.
Potential vulnerabilities automatically “break” the build so that they never surface in our products. Any new vulnerabilities that may impact the system are immediately prioritized and addressed according to the Dremio Vulnerability Management Policy.
Dremio performs regular penetration tests with a trusted, industry-leading third party team which consists of world-class penetration testers and cybersecurity researchers. All vulnerabilities that are found are addressed and retested according to the Dremio Vulnerability Management Policy.
Compliance
Dremio meets the Information Security control requirements for a multitude of compliance frameworks and certifications.
HIPAA
Dremio is HIPAA-ready and enables covered entities and their business associates to use a secure data lake platform to analyze protected health information (PHI) subject to the U.S. Health Insurance Portability and Accountability Act of 1996 (HIPAA).
SOC 2 Type 2
Dremio maintains compliance with American Institute of Certified Public Accountants (AICPA) System and Organization Controls - Trust Services Criteria commonly known as SOC 2.
Dremio makes our SOC 2 Type 2 report available upon request. Please contact your account/sales representative.
ISO 27001
Dremio operates an information security management system (ISMS) that conforms to the requirements stated in the standard: ISO/IEC 27001:2013
Our ISO/IEC 27001 certification is available upon request. Please contact your account/sales representative.



Responsible Disclosure
Security Notifications
Dremio makes all security-related notifications public via Dremio's documents page under the Security Bulletins section.
We also publish an updated list of security fixes for all of our products and services, and include our response to security vulnerabilities impacting Dremio through our supply chain, vendors, and dependencies under the Release Notes.
Vulnerability Reporting
The Dremio Security team takes security findings extremely seriously. We care deeply about the security of our products and the data that they protect. We investigate every reported security vulnerability and take action to remediate and/or mitigate all issues that we encounter.
Dremio encourages responsible security research on our services and products. When reporting a potential vulnerability to Dremio, please include a detailed description of the vulnerability, targets, steps, artifacts (such as web requests, responses and screen captures) in your report.
Dremio does not accept the vulnerabilities listed in our submission limitations page. Please review the responsible disclosure limitations before reporting vulnerabilities to us.
If you believe you’ve identified a security issue, please contact us at [email protected].
Here is our PGP Public key.
Security Resources
End-to-End Data Security
With Dremio, your data and data processing stays in your cloud account, where data is encrypted at rest and in transit. Easily safeguard your data further with dynamic data masking and support for customer-managed encryption keys.
Extensible, Fine-Grained Access Control
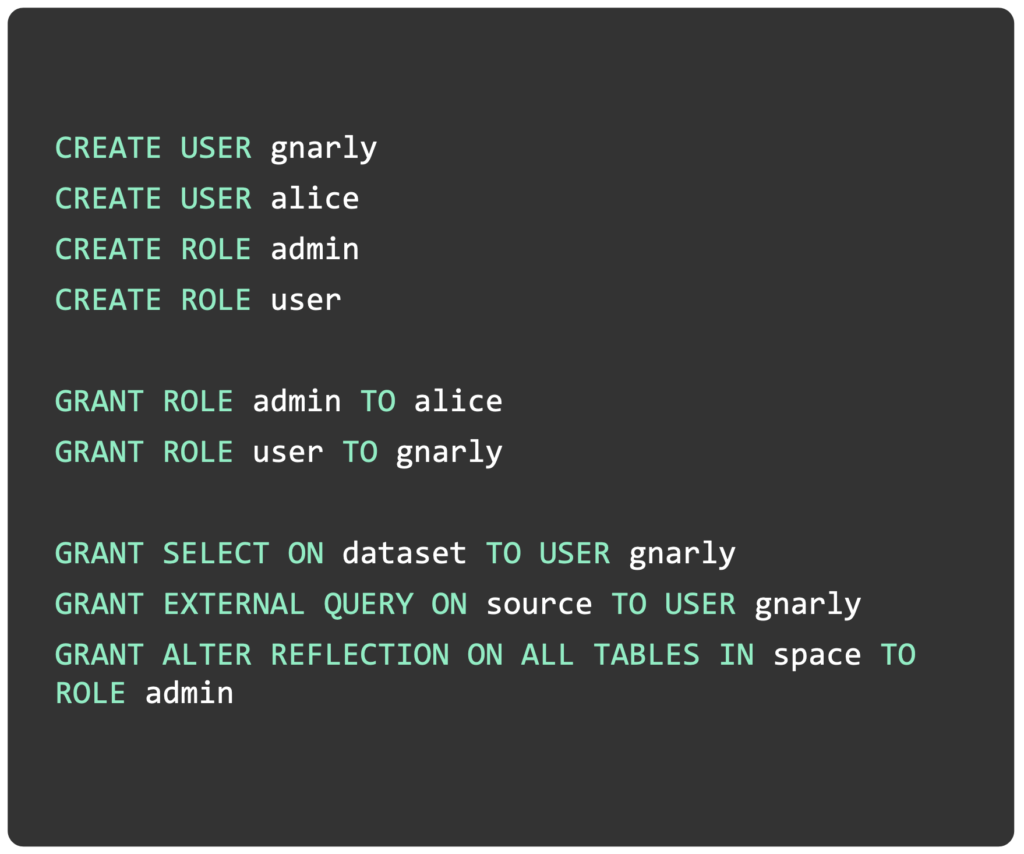
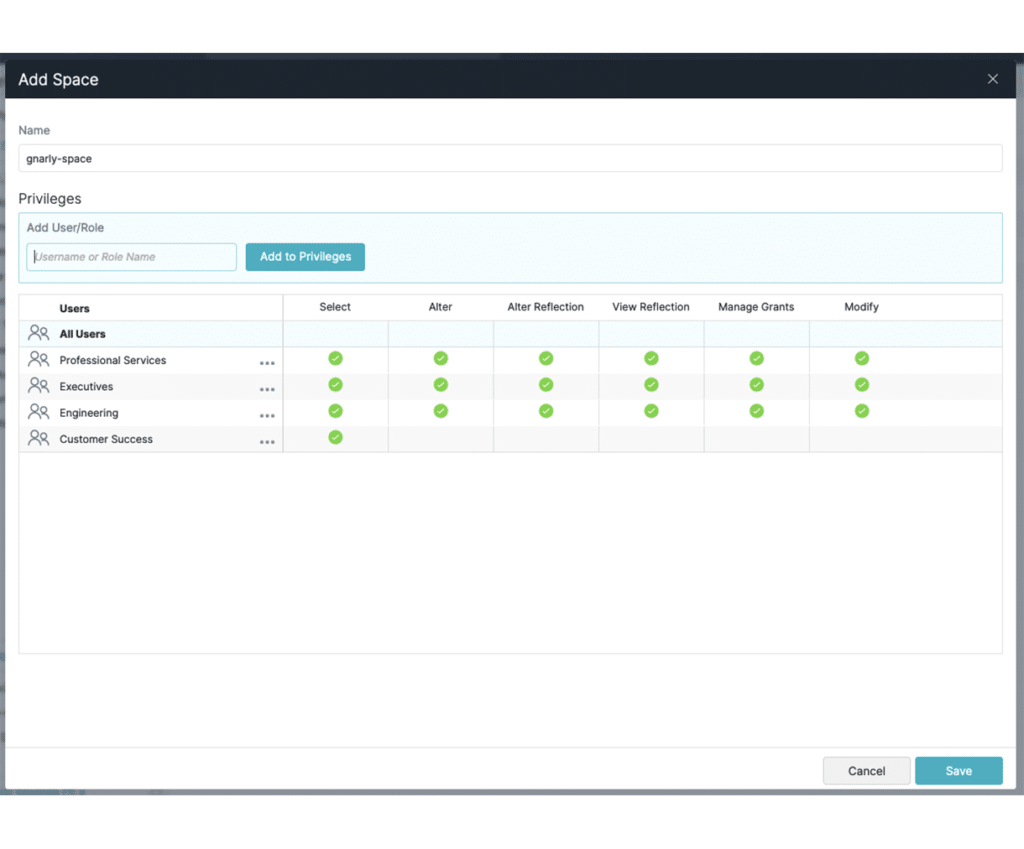
Implement fine-grained, database-style permissions across all Dremio objects with Role-Based Access Control (RBAC). Use ANSI SQL to manage users, grant/revoke privileges, define custom roles, and more. Easily sync existing roles and users in enterprise identity providers like Azure Active Directory, Okta, and Ping via SCIM.
Dremio also integrates with external access control policy services such as Apache Ranger, Privacera, and Okera.
Seamless Authentication
Dremio supports OpenID Connect to authenticate users with any social or corporate identity provider. In addition, OAuth 2.0 and Personal Access Tokens are supported on all interfaces, including programmatic ones (ODBC, JDBC, REST API, and Arrow Flight). With native connectors and SSO in popular BI tools such as Tableau and Power BI, users are automatically authenticated when running queries.
Centralized Security and Governance
Use Dremio’s semantic layer to define centralized security and governance policies over your data lake that can be reused by any downstream tools or applications. The semantic layer enables you to provide different views of data to different users and roles, including row and column-level security.
Dremio Security Resources
If you’d like to learn more about the security features that we’ve built into our products, here are some great resources.
Technical Resources
Dremio Security Policies
Dremio Vulnerability Management Policy
Dremio Security Incident Management Policy